Tytus Kurek
on 3 December 2019
What is Kata Containers and why should I care?
Kata Containers can significantly improve the security and isolation of your container workloads. It combines the benefits of using a hypervisor, such as enhanced security, and container orchestration capabilities provided by Kubernetes.
Together with Eric Erns from Intel, we have recently performed a webinar in which we presented the benefits of using Kata Containers in a Charmed Kubernetes environment. In this blog, we aim to highlight the key outcomes from this webinar.
Security and isolation issues with containers
Over the last few years, container technologies have dominated the market and become the de facto standard for implementing modern IT infrastructure. Because of their lightweight nature and bare-metal-like performance, they are usually preferred over traditional VMs (virtual machines). However, one of the main adoption concerns is around security and isolation.
This is because the traditional OCI runtime – runC – relies on Linux kernel features, such as cgroups and namespaces to provide isolation when spawning containers. As a result, containers share the same kernel which is usually considered less secure than using traditional virtualisation. In order to deal with the aforementioned challenges the Kata Containers project has been founded.
What is Kata Containers?
Wait a second, “What is Kata Containers” or “What are Kata Containers”? It may not be intuitive. This is because Kata Containers is a name of the project under the governance of the OpenStack Foundation. It is also a name of the OCI (Open Container Initiative) runtime which the project uses. So now as we know what is Kata Containers, let’s focus on its architecture and the benefits it brings.
Contrary to the runC runtime, the Kata Containers runtime uses a hypervisor to provide isolation when spawning containers. It creates lightweight VMs and puts containers inside. The figure below demonstrates this concept. As a result, each container runs on its own kernel eliminating security limitations of the traditional runC runtime.
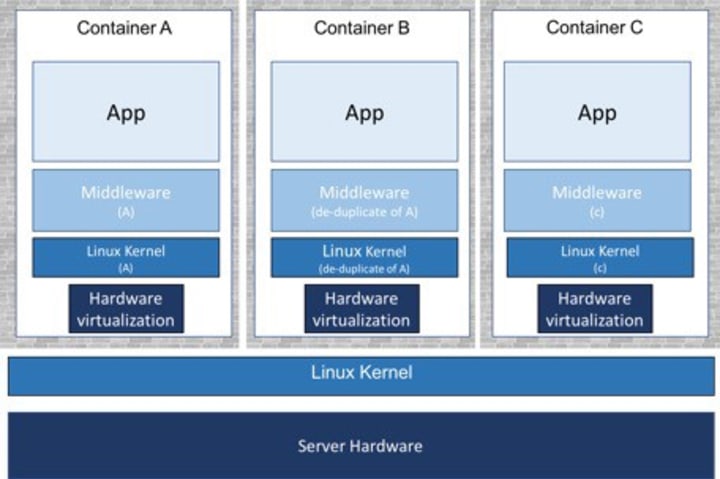
One of the biggest advantages of Kata Containers over traditional VMs is that it seamlessly plugs to existing container orchestration platforms like Kubernetes. While you are launching VMs, native Kubernetes features, such as auto-scaling or rolling updates are still available. This allows to combine the benefits of using virtualisation technology and container orchestration capabilities.
Explore Kata Containers
One of the fastest ways to get started with Kata Containers is to deploy it in the Charmed Kubernetes environment. Once you have Charmed Kubernetes up and running, there are just four commands to deploy this extension:
$ juju deploy cs:~containers/kata
$ juju relate kata kubernetes-master
$ juju relate kata kubernetes-worker
$ juju relate kata:untrusted containerd:untrustedThe first one deploys the Kata Containers runtime, while the other ones configure Kubernetes services to use it. Such an approach is scalable even in clusters consisting of hundreds of nodes.
Once deployed, you can use the new runtime in a very intuitive way. First, create a RuntimeClass object:
$ echo <EOF >> kata.yaml
apiVersion: node.k8s.io/v1beta1
kind: RuntimeClass
metadata:
name: kata
handler: kata
EOF
$ kubectl create -f kata.yaml
runtimeclass.node.k8s.io/kata createdThen you can refer it when creating a pod or deployment. Simply add a runtimeClassName parameter to the spec section of your YAML file and refer to the class you created. for example:
$ cat nginx-kata.yaml
apiVersion: v1
kind: Pod
metadata:
creationTimestamp: null
labels:
run: nginx-kata
name: nginx-kata
spec:
runtimeClassName: kata
containers:
- image: nginx
name: nginx-kata
resources: {}
dnsPolicy: ClusterFirst
restartPolicy: Never
status: {}Now when creating the nginx-kata pod, it will be created using the Kata Containers runtime.
For more more information, read the tutorial: Ensuring security and isolation in Charmed Kubernetes with Kata Containers.
Conclusions
If you are looking for a solution to secure your container workloads while still running them on top of Kubernetes then Kata Containers is the answer. Regardless of the size of your cluster, you can enable the extension in Charmed Kubernetes by running just four commands.
To learn more about Canonical’s solutions for Kubernetes visit our website.
For more information about Kata Containers, refer to the official project website.



